In a digitally transformative world where the end-user experience (EuE) is a #1 business priority, application health and understanding how applications perform, especially in hybrid IT environments with multiple security layers, is critical.
Here are four best practices from the experts at SkyLIGHT™ PVX that can ensure application health in these environments.

Application Health Best Practice #1: Having the right level of plumbing
Start by knowing if you have the right level of plumbing; that is, ensuring that all relevant packets are captured as they travel across the infrastructure.
Since security policies often take precedence when it comes to managing the entire IT infrastructure, when we look at deployment strategies specific to security appliances, we find that most strategies align these appliances with the application streams. Depending upon the company size and other factors, there may be multiple security appliances, which creates additional security zones (or segments).
This calls for the development of a schematic, conceptual overview addressing all branches/remote offices, datacenter(s), and cloud services, including the application flows.
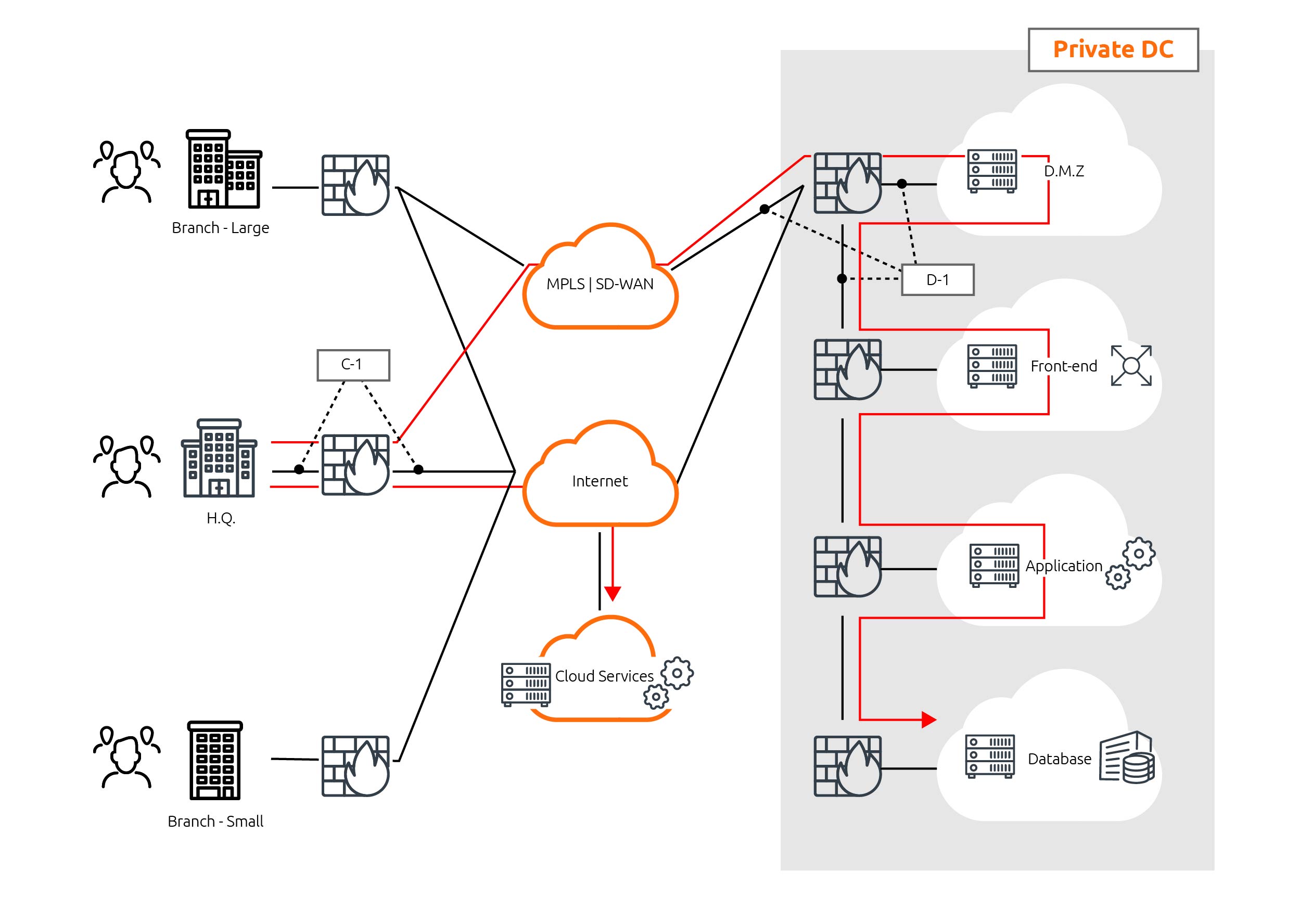
Example of a schematic, conceptual overview of branches, the data center(s), and application flows
In this distributed, multi-segment set-up with its potential traffic volumes, a number-cruncher vs. packet-cruncher approach is preferred. The number-cruncher approach allows for accelerated identification and resolution of application issues impacting users and sites. It also allows for the identification of those security zones/segments that are impacting performance, whether in a negative or positive manner. (See SkyLIGHT PVX white paper on number vs. packet crunching.)
Application Health Best Practice #2: Detailing the plumbing for the datacenter
For larger organizations, often the data center infrastructure includes 10 Gbps network devices with
To collect the packets going in and out of a given security appliance, we believe in installing

The physical aspects of utilizing fiber cabling and a tap
Application Health Best Practice #3: Detailing the plumbing for the branches
So how would this work for the branches/remote locations with 1 Gbps copper connections? It depends. If the aggregated traffic volume of all full-duplex connections is well below 1 Gbps, port mirroring is a consideration. Anything above 1 Gbps requires copper taps.
Application Health Best Practice #4: Checking for leakages
Once the number-cruncher is connected and fired up, start checking for leakages in the plumbing or anywhere else (i.e., dropped packets).
- Check the performance stats of the ESX host; in particular, the stats about dropped packets on the network cards assigned to packet sniffing. These should read all zeroes. If not, it could be either the plumbing or that the hardware of the ESX host cannot keep pace with incoming packets.
- Check the number-cruncher(s) via the CLI command “analyzer,” once expectations are met at the ESX level.
- Check the CPU workload on the number-cruncher(s) using the monitoring graphs of the web-
UI (i.e., if there are dropped packets). Depending on what you uncover, leakages may exist due to a lack of CPU resources. One approach to fixing this is by adding more virtual CPUs.

 Improved delivery, better visibility: How Accedian and VMware are working together to help CSPs navigate the 5G world
Improved delivery, better visibility: How Accedian and VMware are working together to help CSPs navigate the 5G world
 Adding a new dimension of visibility to the Cisco Full-Stack Observability portfolio with Accedian Skylight
Adding a new dimension of visibility to the Cisco Full-Stack Observability portfolio with Accedian Skylight