Cloud network traffic creates new visibility challenges
You might think that by moving workloads to a cloud IaaS (Infrastructure-as-a-Service) platform, that you’ve completely outsourced your infrastructure layers, including the network side, and don’t need cloud performance monitoring.
You might also assume that since you’re not managing the network layer any more, you can use your current on-premise data center network visibility tools and don’t need to deploy a cloud traffic-specific monitoring solution.
There are specific reasons why you will need to have cloud traffic analysis capabilities. Some are old. Some are new and have come with the ubiquitous presence that is the cloud.
Let’s start with the old ones, the reasons you had network monitoring in place within your traditional environment, which remain valid in the cloud:
- Performance troubleshooting: analyzing network traffic has always been a great source of performance analytics to understand end user experience degradations and isolate the source of faults. This remains absolutely true in a cloud environment and that’s a great reason to have cloud network analytics in place.
- Architecture decisions and optimization: there are always multiple ways to deploy infrastructure and applications, including in a cloud IaaS environment. Where will you locate which resources, across how many regions and VPCs? These choices come with consequences in terms of complexity, economics and impact on end user experience. Cloud network forensics help you evaluate these options on the 3 dimensions and optimize your architecture.
- Security monitoring: security often starts with visibility and having a clear picture of who does what, where and when. Both for threat detection and incident investigations, cloud network forensics have a great advantage on other data sources. Cloud network logs cannot be erased or cleaned by an attacker. What is reported from the network is undoubtedly what happened.
Finally there is a new and very important reason to have some form of cloud network telemetry in place: cost!
- In the days of traditional data centers, you invested into a certain network capacity (10Gbps, 40Gbps, or 100Gbps connectivity) until you reached that limit the marginal cost of any new east-west traffic would be zero.
- In a cloud environment, while you have an (almost) unlimited scalability, every byte you carry comes at a cost. All traffic that is uncontrolled or illegitimate will also be reported on your cloud bill.
This is a major risk in complex and dynamic environment as cost becomes unpredictable. Knowing about cloud traffic flows becomes crucial to:
- Avoid misconfigurations leading to increased cloud bandwidth costs
- Optimize cloud bandwidth costs
- Receive alerts of any changes in behavior or abnormal cloud traffic and anomalies
What are the potential approaches to cloud traffic monitoring?
There are two main ways to analyze cloud traffic:
- Use the metadata provided by Cloud Providers
Good examples are AWS VPC Flows and Microsoft Azure Network Watcher. They basically provide you with network logs in a form which is similar to traditional Netflow records. That metadata will usually be charged by hour and/or GB. - Capturing packets in the cloud
Access to a genuine copy of the production traffic in the cloud. The new challenge compared to an on-premise data center is that we do not have access to the network layer and cannot use any form of a SPAN.
The workaround will consist of placing either an agent or a system component to get access to the copy of the traffic. The difference between an agent and a system component is that some data processing is executed in the production system, frequently generating increased system resource consumption. System components redirecting the traffic to a network analyzer are also referred to as Cloud vTAPs.
Some examples are:
- Agents
- Netscout vScout
- Agent-based application performance monitoring (APM) systems
- Dynatrace OneAgent
- AppDynamics
- NewRelic
- System components and vTAPs
- Ixia
- CloudLens
- Gigamon GigaVUE
- An opensource component
- RPCAPD
- A cloud packet broker
- Accedian Skylight
The pros and cons of these cloud traffic monitoring approaches
| Pros | Cons | |
| Cloud flows (metadata) | No instrumentation of production instances | Limited to who talks to whom for specific volumes No performance metrics or precise data for performance troubleshooting or application level visibility |
| Packet-based data | Ultra precise data performance metrics Application transaction visibility | Requires the implementation of an agent or a system component vTap on the production instances |
Accedian’s Skylight solution provides complete visibility for all “east-west” and “north-south” transaction traffic in the cloud. This enables you to rapidly detect performance degradations, anomalous behaviour, and other issues that can negatively impact your cloud applications.
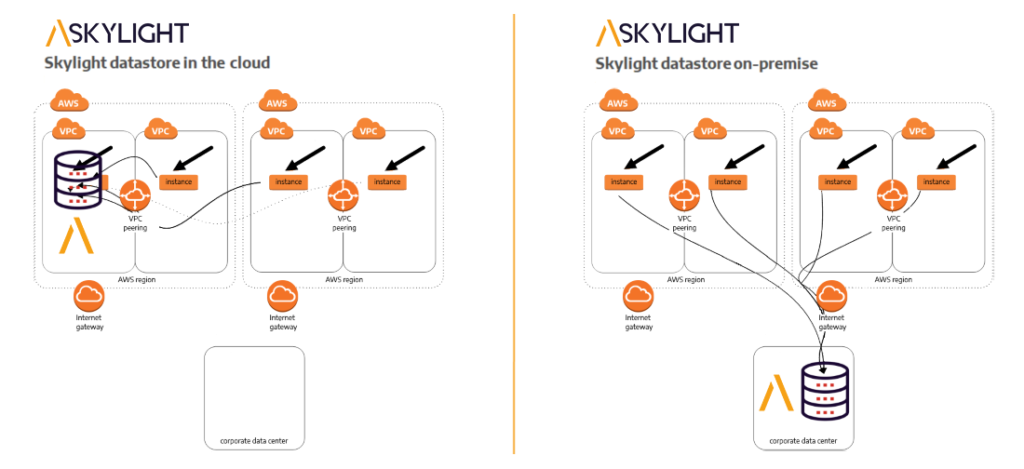
Learn how Accedian Skylight provides outstanding value as a cloud performance monitoring solution. See how Skylight’s exceptional metadata provides the best TCO for any cloud performance monitoring solution.
You might also be interested in our blog post How to Configure AWS VPC Traffic Mirroring, which provides a step by step guide about how to take advantage of this important new AWS feature.

 Improved delivery, better visibility: How Accedian and VMware are working together to help CSPs navigate the 5G world
Improved delivery, better visibility: How Accedian and VMware are working together to help CSPs navigate the 5G world
 Adding a new dimension of visibility to the Cisco Full-Stack Observability portfolio with Accedian Skylight
Adding a new dimension of visibility to the Cisco Full-Stack Observability portfolio with Accedian Skylight