A well-planned cyber attack against a government or large business is a frightening prospect. Particularly when the attack is designed to infiltrate a network over a long time period to steal sensitive data. This type of campaign is known as an advanced persistent threat (APT) and it has become a common occurrence on today’s complex networks.
Once the domain of state-sponsored cyber terrorist groups focused on infiltrating governments and large businesses and political organizations, APTs have evolved to become a more common form of cyberattack.
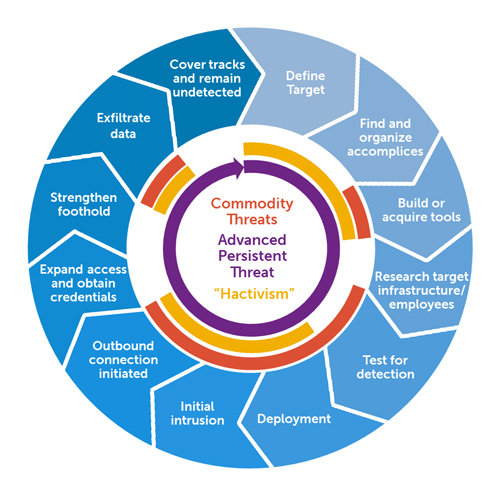
How an APT is carried out
Businesses and organizations at risk for an APT attack should be aware of how these types of malicious events are carried as a means to successfully detect, combat and prevent them.
An APT begins when a malicious person or group gains access to a network. This is typically accomplished through an email, file or application vulnerability. The attacker then installs malware within the network, putting it at risk.
The role of the malware is to find additional vulnerabilities and network access. The malware will then set up other points of compromise to ensure the APT is successful if one point is discovered and closed off. The group that placed the malware then will work to mine sensitive data and collect it on a staging server. The data is then moved off the network and the network is officially breached.
At this point, the attacker can remove evidence of the attack while maintaining access to the network.
APT attacks are extremely dangerous for organizations, and they require a coordinated and skilled effort on the part of the attacker. The perpetrators are typically government-sponsored or backed financially by larger criminal organizations.
An attack can last months or possibly years without proper detection and mitigation. The main goals of these types of attacks include:
- Theft of intellectual property
- Theft of sensitive data such as employee user names and passwords
- Sabotage of critical infrastructure like database deletion
- Sabotage of surveillance systems
- Complete site takeover
Signs of an APT attack
Early detection of APT attacks is critical for successful mitigation before networks are truly compromised and sensitive data is exposed. While these types of attacks can be sneaky and difficult to detect, there are a number of red flags security teams should be on the lookout for:
- Unexpected logins
A large number of server logins outside of regular office hours may indicate an APT attack is happening. A common network entry method for the attacks is by using stolen login credentials.
2. Increased spear-phishing emails
Spear phishing is the practice of sending emails fraudulently through a known sender. The goal is to get recipients to reveal confidential information and documents. A large number of these types of emails, particularly when sent to individuals in upper management, may be part of a coordinated APT attack.
3. Unauthorized data movement
APT attackers often copy data to another location on the network before stealing it. This helps ensure they may move the data off network without being noticed. Any unexplained or unauthorized movement of data should be immediately investigated.
4. Increased back-door Trojan activity
A backdoor Trojan enables attackers to gain remote control of an infected computer. The attacker may then do whatever they wish on that machine, including stealing or deleting files. An increase in this type of activity may indicate a broader APT attack.
Detection and mitigation of APTs
When it comes to protecting against APT attacks, traditional security methods like firewalls and antivirus software simply can’t handle the job. A comprehensive behavior-based intrusion detection system (IDS) can find and mitigate APTs before the network is compromised.
Behavior-based IDS solutions work by detecting vulnerability exploits against a computer, application or network. They take advantage of machine learning and intelligent data to provide complete network traffic analysis. This enables full visibility of all suspicious activities occurring throughout the network. These types of offerings work alongside network perimeter protection solutions to enable a holistic and thorough approach to network security and an organization’s cyber resiliency.
One of the key benefits of behavior-based IDS is the built-in network traffic analytics that is core to the solution. Intelligent analysis of network traffic can pinpoint behavior patterns and then monitor and build baselines for those behaviors. Once these are established, all new network activity is compared to the baseline to easily weed out anomalous and nefarious behaviors.
APT attacks are frightening and potentially dangerous—but they don’t have to be. Organizations that take the proper steps to identify and combat the various components of an APT attack can cut off attacker access before data is stolen and the network is compromised.
The right tools are essential for identifying and fighting this type of attack. A next-generation, behavior-based IDS offering is a powerful security weapon for combating an APT attack as well as protecting the network at large. Accedian’s Next-Gen Intrusion Detection guide offers additional information about how the proper IDS tools can help combat APT and other cyber attacks while offering a holistic view of any growing network.

 Improved delivery, better visibility: How Accedian and VMware are working together to help CSPs navigate the 5G world
Improved delivery, better visibility: How Accedian and VMware are working together to help CSPs navigate the 5G world
 Adding a new dimension of visibility to the Cisco Full-Stack Observability portfolio with Accedian Skylight
Adding a new dimension of visibility to the Cisco Full-Stack Observability portfolio with Accedian Skylight